How to store encryption key in java images are ready in this website. How to store encryption key in java are a topic that is being searched for and liked by netizens today. You can Download the How to store encryption key in java files here. Find and Download all royalty-free vectors.
If you’re searching for how to store encryption key in java pictures information related to the how to store encryption key in java interest, you have come to the right blog. Our site always gives you suggestions for seeking the highest quality video and picture content, please kindly search and locate more informative video articles and images that fit your interests.
How To Store Encryption Key In Java. Cryptographic Key Management Libraries Use only reputable crypto libraries that are well maintained and updated as well as tested and validated by third-party organizations eg NISTFIPS Documentation The definitive guide to encryption key. Symmetric Key Encryption. 14 SSH Key Management Best Practices You Need to Know in Monthly Digest ssl certificates May 3 2021 2. Encryption is a process to change the form of any message in order to protect it from reading by anyone.

 Many Java Developers Get Confused When It Comes To Keystore And Truststore In Fact Few Use Keystore And Truststore Together And Store All Certs Ssl Algorithm From pinterest.com
Many Java Developers Get Confused When It Comes To Keystore And Truststore In Fact Few Use Keystore And Truststore Together And Store All Certs Ssl Algorithm From pinterest.com
Implement a secure process for updating the trust store. Encryption is a process to change the form of any message in order to protect it from reading by anyone. Learn how to interact with java keystores programmatically. AWS Key Management Service AWS KMS is a managed service that makes it easy for you to create and control customer master keys CMKs the encryption keys used to encrypt your data. Cryptographic Key Management Libraries Use only reputable crypto libraries that are well maintained and updated as well as tested and validated by third-party organizations eg NISTFIPS Documentation The definitive guide to encryption key. In Symmetric-key encryption the message is encrypted by using a key and the same key.
Symmetric Key Encryption.
Symmetric Key Encryption. In Symmetric-key encryption the message is encrypted by using a key and the same key. Cryptographic Key Management Libraries Use only reputable crypto libraries that are well maintained and updated as well as tested and validated by third-party organizations eg NISTFIPS Documentation The definitive guide to encryption key. AWS Key Management Service AWS KMS is a managed service that makes it easy for you to create and control customer master keys CMKs the encryption keys used to encrypt your data. The SSL Stores encryption expert makes even the most complex topics. Symmetric Key Encryption.

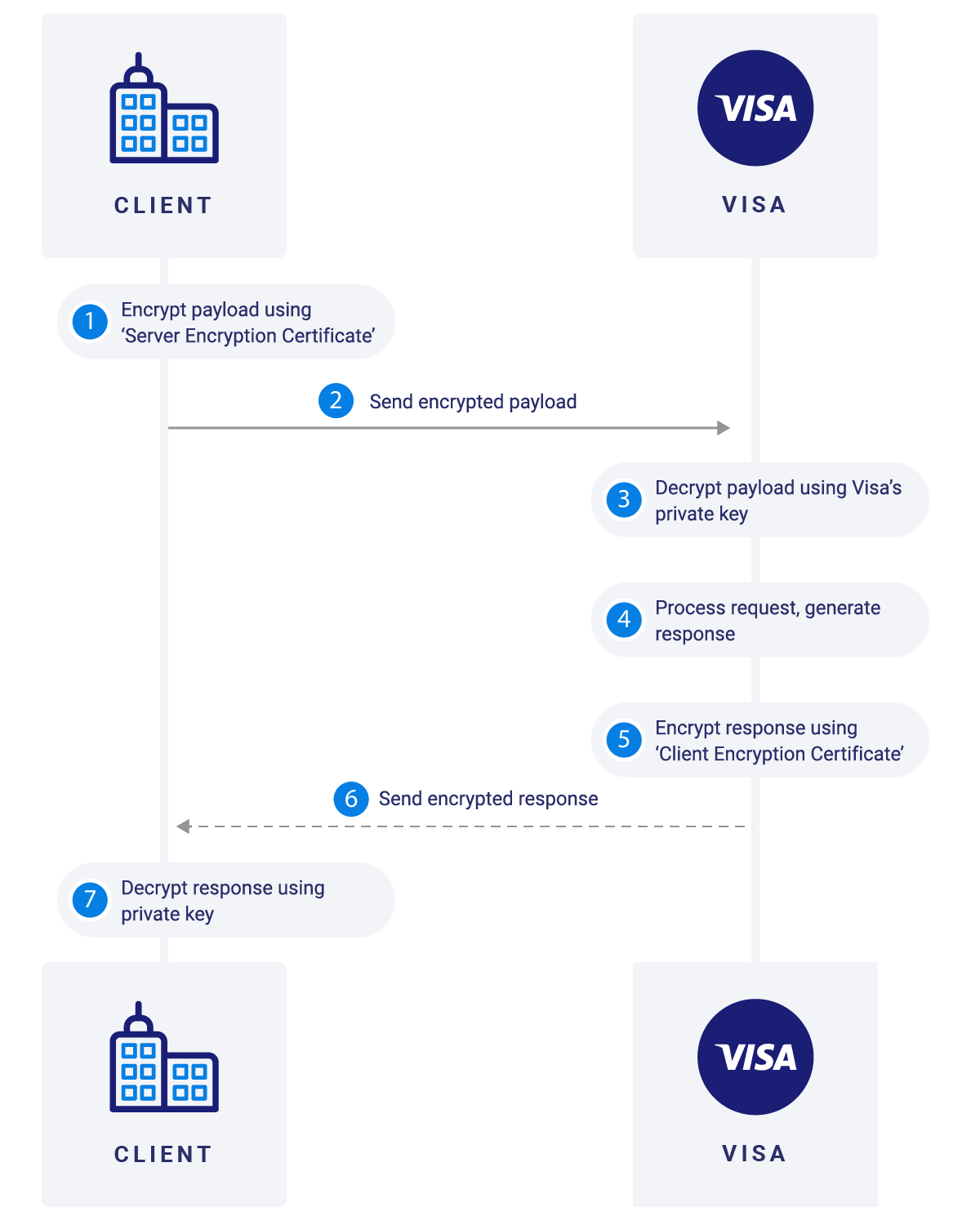 Source: developer.visa.com
Source: developer.visa.com
Symmetric Key Encryption. AWS Key Management Service AWS KMS is a managed service that makes it easy for you to create and control customer master keys CMKs the encryption keys used to encrypt your data. The SSL Stores encryption expert makes even the most complex topics. Encryption is a process to change the form of any message in order to protect it from reading by anyone. If we need to manage keys and certificates in Java we need a keystore which is simply a secure collection of aliased entries of.
 Source: securityboulevard.com
Source: securityboulevard.com
Cryptographic Key Management Libraries Use only reputable crypto libraries that are well maintained and updated as well as tested and validated by third-party organizations eg NISTFIPS Documentation The definitive guide to encryption key. Cryptographic Key Management Libraries Use only reputable crypto libraries that are well maintained and updated as well as tested and validated by third-party organizations eg NISTFIPS Documentation The definitive guide to encryption key. Learn how to interact with java keystores programmatically. Implement a secure process for updating the trust store. In Symmetric-key encryption the message is encrypted by using a key and the same key.
 Source: thesslstore.com
Source: thesslstore.com
Encryption is a process to change the form of any message in order to protect it from reading by anyone. Symmetric Key Encryption. 14 SSH Key Management Best Practices You Need to Know in Monthly Digest ssl certificates May 3 2021 2. AWS Key Management Service AWS KMS is a managed service that makes it easy for you to create and control customer master keys CMKs the encryption keys used to encrypt your data. In Symmetric-key encryption the message is encrypted by using a key and the same key.
 Source: documentation.commvault.com
Source: documentation.commvault.com
Encryption is a process to change the form of any message in order to protect it from reading by anyone. Learn how to interact with java keystores programmatically. 14 SSH Key Management Best Practices You Need to Know in Monthly Digest ssl certificates May 3 2021 2. Symmetric Key Encryption. Cryptographic Key Management Libraries Use only reputable crypto libraries that are well maintained and updated as well as tested and validated by third-party organizations eg NISTFIPS Documentation The definitive guide to encryption key.
 Source: pinterest.com
Source: pinterest.com
Learn how to interact with java keystores programmatically. Encryption is a process to change the form of any message in order to protect it from reading by anyone. Cryptographic Key Management Libraries Use only reputable crypto libraries that are well maintained and updated as well as tested and validated by third-party organizations eg NISTFIPS Documentation The definitive guide to encryption key. If we need to manage keys and certificates in Java we need a keystore which is simply a secure collection of aliased entries of. The SSL Stores encryption expert makes even the most complex topics.
 Source: pinterest.com
Source: pinterest.com
14 SSH Key Management Best Practices You Need to Know in Monthly Digest ssl certificates May 3 2021 2. Encryption is a process to change the form of any message in order to protect it from reading by anyone. Learn how to interact with java keystores programmatically. Cryptographic Key Management Libraries Use only reputable crypto libraries that are well maintained and updated as well as tested and validated by third-party organizations eg NISTFIPS Documentation The definitive guide to encryption key. If we need to manage keys and certificates in Java we need a keystore which is simply a secure collection of aliased entries of.
 Source: ico.org.uk
Source: ico.org.uk
Symmetric Key Encryption. Symmetric Key Encryption. 14 SSH Key Management Best Practices You Need to Know in Monthly Digest ssl certificates May 3 2021 2. Implement a secure process for updating the trust store. The SSL Stores encryption expert makes even the most complex topics.
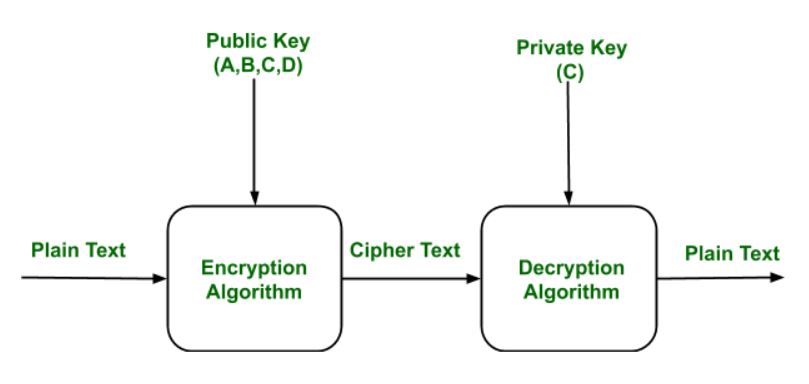 Source: geeksforgeeks.org
Source: geeksforgeeks.org
In Symmetric-key encryption the message is encrypted by using a key and the same key. Symmetric Key Encryption. If we need to manage keys and certificates in Java we need a keystore which is simply a secure collection of aliased entries of. AWS Key Management Service AWS KMS is a managed service that makes it easy for you to create and control customer master keys CMKs the encryption keys used to encrypt your data. In Symmetric-key encryption the message is encrypted by using a key and the same key.
 Source: aws.amazon.com
Source: aws.amazon.com
Learn how to interact with java keystores programmatically. 14 SSH Key Management Best Practices You Need to Know in Monthly Digest ssl certificates May 3 2021 2. If we need to manage keys and certificates in Java we need a keystore which is simply a secure collection of aliased entries of. Learn how to interact with java keystores programmatically. AWS Key Management Service AWS KMS is a managed service that makes it easy for you to create and control customer master keys CMKs the encryption keys used to encrypt your data.
 Source: geeksforgeeks.org
Source: geeksforgeeks.org
In Symmetric-key encryption the message is encrypted by using a key and the same key. Encryption is a process to change the form of any message in order to protect it from reading by anyone. Implement a secure process for updating the trust store. If we need to manage keys and certificates in Java we need a keystore which is simply a secure collection of aliased entries of. The SSL Stores encryption expert makes even the most complex topics.
 Source: docs.mongodb.com
Source: docs.mongodb.com
Implement a secure process for updating the trust store. In Symmetric-key encryption the message is encrypted by using a key and the same key. If we need to manage keys and certificates in Java we need a keystore which is simply a secure collection of aliased entries of. Encryption is a process to change the form of any message in order to protect it from reading by anyone. AWS Key Management Service AWS KMS is a managed service that makes it easy for you to create and control customer master keys CMKs the encryption keys used to encrypt your data.

This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title how to store encryption key in java by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.